WordPress powers a substantial percentage of the web, with 43.1% of all websites using it as their content management system. (Source: WPZoom) This popularity makes WordPress sites prime targets for hackers and malicious actors. As a web design and development agency, we’ve seen firsthand how WordPress security challenges have evolved over the years.
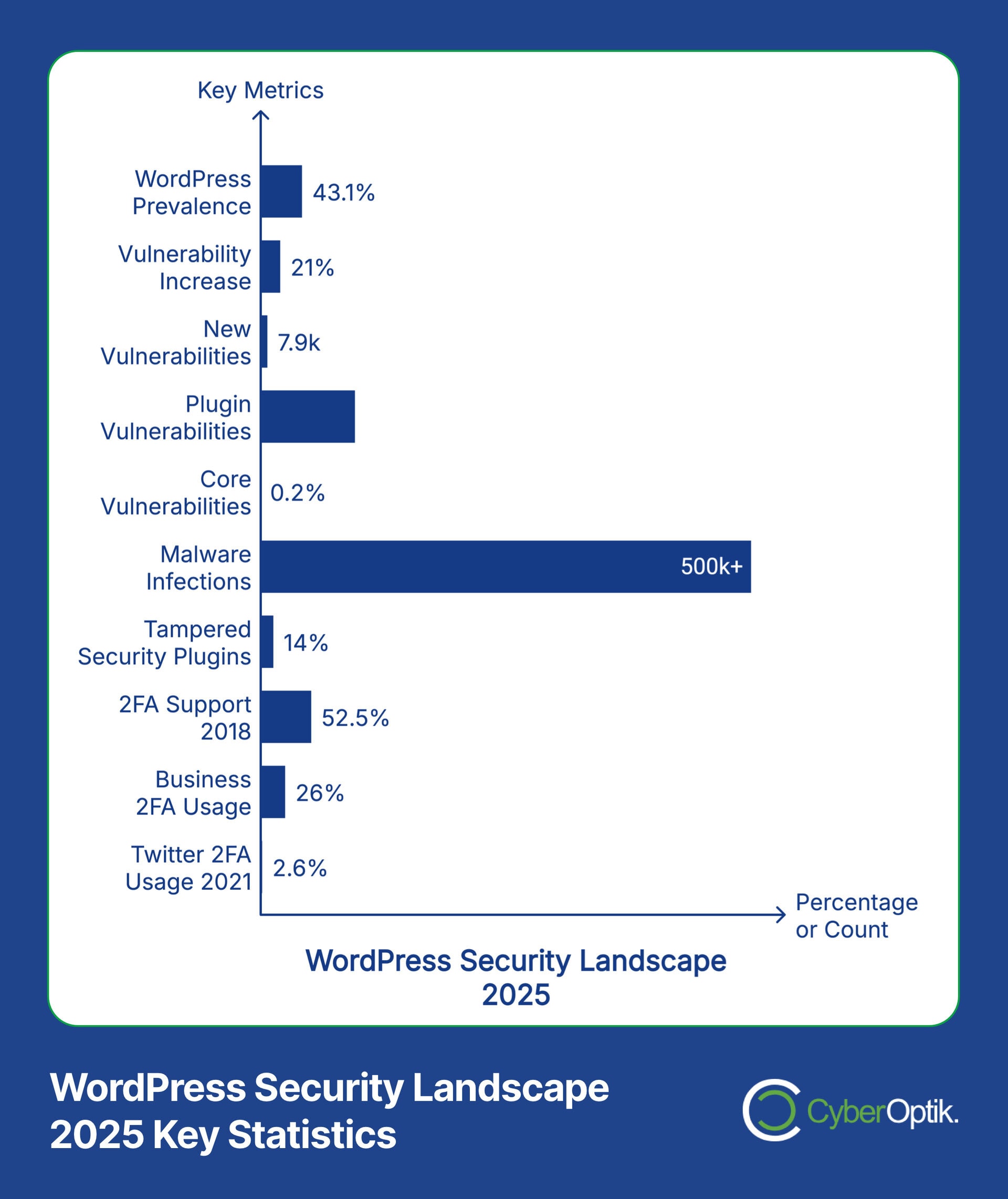
The security threat landscape continues to intensify, with a 21% increase in vulnerabilities reported in 2024 compared to 2023. (Source: The Admin Bar) These statistics highlight the growing importance of implementing strong security measures for your WordPress website.
What many website owners don’t realize is that plugins represent the greatest vulnerability in WordPress websites. In fact, 97% of WordPress vulnerabilities stem from plugins rather than the core software. (Source: Patchstack) This makes your choice of security plugins particularly crucial for maintaining a secure website.
The risk of WordPress sites getting hacked continues to increase as attackers develop more sophisticated methods. Two-factor authentication has emerged as a critical defense against these growing threats, providing an essential security layer that goes beyond traditional password protection.
Understanding Two-Factor Authentication (2FA)
Two-factor authentication, commonly abbreviated as 2FA, adds an additional security layer to your login process. It requires users to prove their identity in two different ways before gaining access to your WordPress dashboard or other protected areas.
How 2FA Works in WordPress
The standard login process requires only a username and password. With 2FA, after entering these credentials correctly, users must provide a second verification factor. This significantly reduces the risk of unauthorized access, even if passwords are compromised.
To illustrate the severity of current threats, consider that over 500,000 WordPress sites were infected with malware in 2024 alone. (Source: Patchstack) Many of these infections could have been prevented with proper 2FA implementation.
While 2FA adoption continues to grow, there’s still considerable room for improvement. Studies show that 52.5% of sites supported 2FA as of 2018, with no significant growth since 2014. (Source: Elie.net) This relatively slow adoption rate persists despite the clear security benefits.
Common Types of 2FA Methods
| 2FA Method | Description | Security Level | User Experience |
|---|---|---|---|
| SMS/Text Messages | Code sent via text message | Moderate | Good (familiar to most users) |
| Authenticator Apps | Time-based code from mobile app | High | Good (works offline) |
| Email Verification | Code or link sent via email | Moderate | Good (no additional app needed) |
| Hardware Tokens | Physical device generating codes | Very High | Moderate (requires carrying device) |
| Biometric | Fingerprint or facial recognition | High | Excellent (quick verification) |
Each 2FA method has distinct advantages and appropriate use cases. For most WordPress sites, authenticator apps offer the best balance of security and convenience. They don’t rely on cell service like SMS, work offline, and provide excellent protection against common attack vectors.
Why Your WordPress Site Needs 2FA
The importance of implementing 2FA for WordPress cannot be overstated in today’s threat environment. In 2024 alone, there were 7,966 new vulnerabilities discovered in the WordPress ecosystem, representing a 34% increase over the previous year. (Source: Patchstack) This alarming trend makes additional security layers essential.
One significant advantage of 2FA is its ability to protect against the most common attack vector: compromised credentials. Even if a hacker obtains a user’s password through phishing, data breaches, or brute force attacks, they still cannot access the account without the second factor.
Business Impact of Security Breaches
For businesses, the consequences of a WordPress security breach extend far beyond the immediate technical issues:
- Data loss or theft – Sensitive customer information may be compromised
- Reputation damage – Customer trust erodes when security incidents become public
- Recovery costs – Cleaning infected sites and restoring data is time-consuming and expensive
- Revenue loss – Downtime during recovery directly impacts sales and lead generation
- SEO penalties – Google may blacklist compromised sites, destroying search visibility
When considering these potential impacts, the minimal effort required to implement 2FA represents an extremely favorable risk-reward proposition. This is especially true when you consider that WordPress core software accounts for just 0.2% of vulnerabilities, with the vast majority coming from third-party code. (Source: Kinsta) This makes user access security even more critical, as it protects against vulnerabilities you may not control directly.
What security tools does your WordPress site need beyond 2FA? While two-factor authentication provides excellent protection for the login process, comprehensive security requires multiple layers of defense, including regular updates, security scanning, and proper hosting configurations.
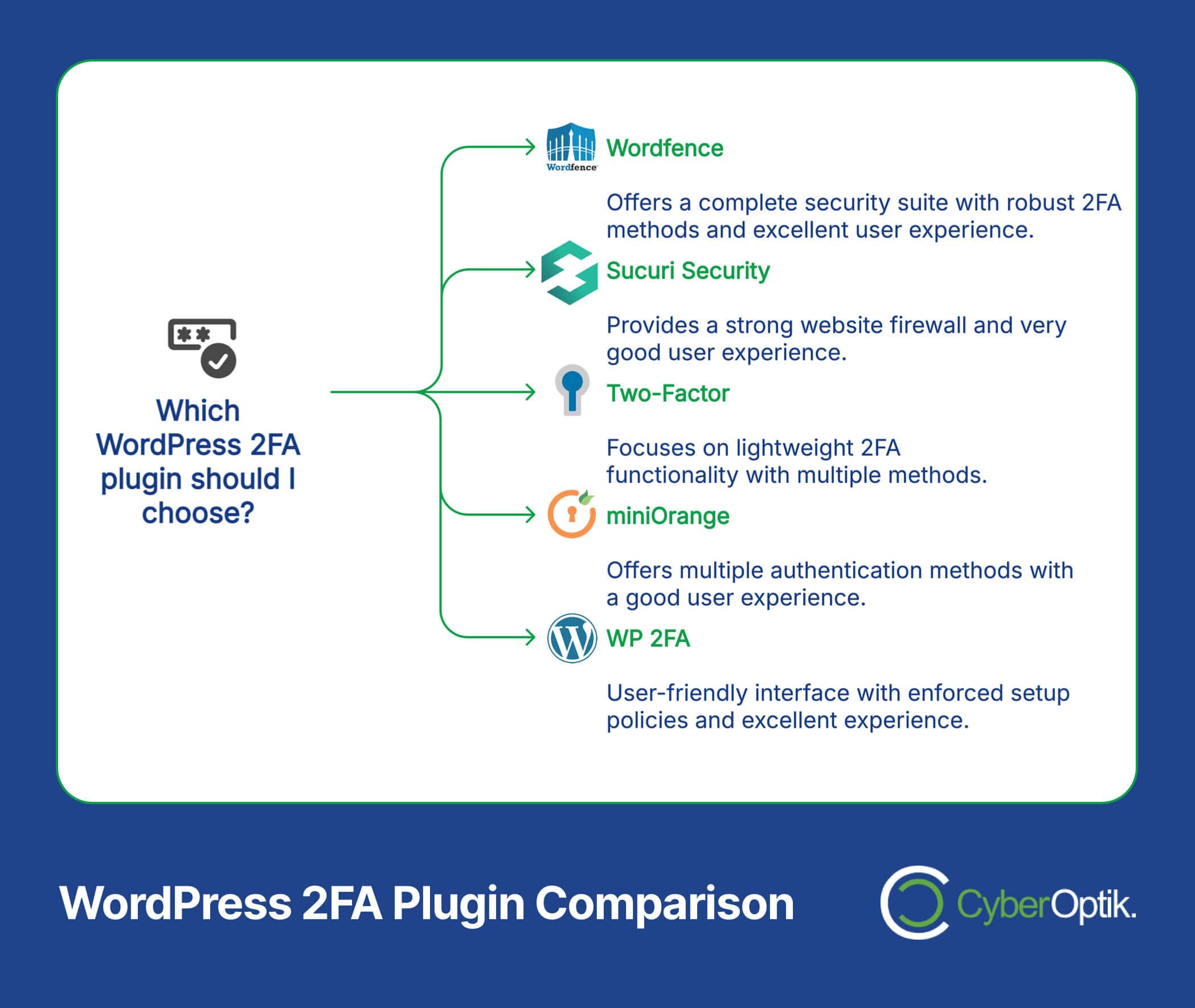
Top WordPress 2FA Plugins Compared
With WordPress plugins being responsible for most security vulnerabilities, choosing reliable, well-maintained security solutions is critical. The plugin ecosystem continues to grow, with over 59,000 free plugins available in the WordPress repository. (Source: WebFX) This abundance of options makes selecting the right 2FA solution challenging.
When evaluating 2FA plugins, it’s important to consider that 14% of malware infections in WordPress sites tampered with security plugin installations, particularly targeting Wordfence. (Source: Patchstack) This emphasizes the importance of choosing plugins from reputable developers with strong security practices.
Below, we’ve compared the top WordPress 2FA plugins available in 2025 to help you make an informed decision:
| Plugin Name | Key Features | Supported 2FA Methods | Free/Premium | User Experience |
|---|---|---|---|---|
| Wordfence | Complete security suite with 2FA, firewall, malware scanning | Email, Authenticator Apps | Free + Premium ($99/year) | Excellent |
| Sucuri Security | Website firewall, security hardening, post-hack tools | Authenticator Apps | Free + Premium ($199/year) | Very Good |
| Two-Factor | Lightweight, focused 2FA functionality | Email, SMS, Authenticator Apps, Hardware Tokens | Free | Good |
| miniOrange | Multiple authentication methods, role-based setup | SMS, Email, Authenticator Apps, Hardware Tokens, Biometric | Free + Premium (from $79/year) | Good |
| WP 2FA | User-friendly interface, enforced setup policies | Email, Authenticator Apps | Free + Premium ($79/year) | Excellent |
Each of these plugins has unique strengths. For most small to medium-sized business websites, we recommend starting with the free version of Wordfence or Two-Factor. For larger organizations or websites with sensitive data, the premium versions of Wordfence or Sucuri provide the most comprehensive protection.
Detailed Feature Comparison
| Feature | Wordfence | Sucuri | Two-Factor | miniOrange | WP 2FA |
|---|---|---|---|---|---|
| Role-based 2FA Enforcement | ✓ (Premium) | ✓ | ✓ | ✓ | ✓ |
| Backup Codes | ✓ | ✓ | ✓ | ✓ | ✓ |
| Login Attempt Limiting | ✓ | ✓ | ✗ | ✓ | ✓ |
| Trusted Devices | ✓ (Premium) | ✓ (Premium) | ✗ | ✓ (Premium) | ✓ (Premium) |
| White-label Option | ✗ | ✓ (Premium) | ✗ | ✓ (Premium) | ✓ (Premium) |
| Integration with Other Plugins | Limited | Good | Limited | Excellent | Good |
This detailed comparison helps you determine which plugin best fits your specific needs. The right choice depends on factors like your website size, user base, technical expertise, and security requirements.
Key Features to Look for in 2FA Plugins
When selecting a 2FA plugin for WordPress, certain features are more important than others. According to authentication standards research, 82.1% of 2FA implementations use software tokens, making this the most prevalent authentication method. (Source: Elie.net) This suggests that support for authenticator apps should be a priority when evaluating plugins.
Essential Security Features
- Multiple authentication methods – Offering choices improves user adoption
- Backup codes or alternative access methods – Critical for account recovery
- Role-based implementation – Apply different requirements based on user roles
- Brute force protection – Block repeated failed login attempts
- Secure implementation – Uses encryption and secure coding practices
User Experience Considerations
User experience directly impacts 2FA adoption rates. The best plugins balance security with usability by including:
- Simple setup process with clear instructions
- Minimal login flow disruption
- Remember device options for trusted computers
- Customizable prompts and messages
- Mobile-friendly authentication screens
The concept of layered security approaches should inform your overall strategy. Two-factor authentication works best when combined with other security measures like regular updates, strong password policies, and secure hosting.
Implementation Best Practices
Implementing 2FA effectively requires careful planning and execution. To understand the stakes, consider that Wordfence alone has blocked 18.5 billion password attacks against WordPress sites. (Source: WebFX) This staggering number illustrates why password protection alone is insufficient.
Step-by-Step 2FA Implementation Guide
- Select the appropriate plugin based on your specific needs
- Install and activate the plugin through your WordPress dashboard
- Configure global settings including which user roles require 2FA
- Set up administrator accounts first to test the system
- Create documentation for other users with setup instructions
- Enable 2FA for all required users in phases to manage support needs
- Establish recovery procedures for lost devices or access issues
A critical consideration during implementation is having backup access methods. Studies show that 39.1% of hacked CMS sites ran outdated software, emphasizing the importance of maintaining all security systems. (Source: Kinsta) This includes keeping your 2FA plugin updated and regularly reviewing its configuration.
Going Deeper
Discover how secure hosting practices complement 2FA protection. Even the best authentication system can be compromised if your hosting environment has vulnerabilities.
Training Users and Managing Adoption
For organizations with multiple WordPress users, training and adoption management are key to successful implementation:
| Challenge | Solution |
|---|---|
| User resistance to change | Explain benefits, provide clear instructions, offer support |
| Setup difficulties | Create step-by-step guides with screenshots, video tutorials |
| Lost devices or access | Establish clear recovery procedures, provide backup codes |
| Different device types | Test across various devices, browsers, and OS versions |
| Legacy system integration | Phase implementation, thorough testing with connected systems |
For multi-user WordPress installations, we recommend a phased rollout approach, starting with technical users and gradually expanding to others. This minimizes disruption and allows for adjustments based on initial feedback.
Common 2FA Challenges and Solutions
Despite its security benefits, implementing 2FA can present certain challenges. Low adoption rates highlight this issue – only 2.6% of Twitter accounts used 2FA in 2021, despite it being freely available. (Source: WPExplorer) Understanding common obstacles and how to overcome them is crucial for successful implementation.
Balancing Security with Convenience
The primary challenge with any security measure is balancing protection with user convenience. Too much friction in the login process can lead to frustration and resistance.
| Challenge | Solution |
|---|---|
| Login process feels too lengthy | Implement "remember this device" options for trusted computers |
| Users forget their second factor | Provide backup codes and clear recovery options |
| Resistance to installing authenticator apps | Offer multiple 2FA methods including email |
| Managing 2FA across multiple sites | Recommend password managers with 2FA support |
A concerning trend in the WordPress ecosystem is the abandonment of plugins. Research found that 58.16% of abandoned plugins were removed from the WordPress repository, potentially leaving sites with outdated security measures. (Source: Patchstack) This highlights the importance of selecting 2FA plugins with active development and regular updates.
Technical Troubleshooting
Even with careful implementation, technical issues can arise:
- Sync problems – Time-based authentication apps may desynchronize
- Plugin conflicts – 2FA plugins may conflict with other security measures
- Cache issues – Server or browser caching can interfere with authentication
- Mobile compatibility – Some implementations work poorly on certain devices
- Lost access recovery – Administrator lockouts require special recovery procedures
For agencies managing multiple client sites, we recommend maintaining emergency access protocols for each website. This ensures you can recover access even if primary authentication methods fail.
Future of WordPress Authentication Security
The authentication landscape continues to evolve rapidly. Only 26% of businesses currently use multifactor authentication, indicating significant room for growth and improvement. (Source: WPExplorer) As security threats increase in sophistication, we expect 2FA adoption to accelerate considerably.
Regulatory Requirements
Security regulations increasingly mandate stronger authentication. The EU Cyber Resilience Act, for instance, will mandate vulnerability reporting by 2026. (Source: Patchstack) This regulatory trend will likely continue, potentially making 2FA a mandatory requirement for websites handling user data.
Emerging Authentication Technologies
Looking forward, several technologies are poised to enhance or replace current 2FA methods:
| Technology | Description | Potential Impact |
|---|---|---|
| Passwordless Authentication | Eliminating passwords entirely in favor of biometrics and tokens | Simplified login with enhanced security |
| Biometric Authentication | Using fingerprints, facial recognition, or other biological identifiers | More convenient, harder to forge |
| Risk-Based Authentication | Adjusting security requirements based on behavioral and contextual signals | Less friction for legitimate users, more for suspicious activity |
| WebAuthn Standard | Open standard for secure authentication using public key cryptography | More secure, phishing-resistant authentication |
These emerging technologies promise to address many current limitations in 2FA implementations, particularly around user experience. WordPress development will likely incorporate these advances as they mature and gain wider adoption.
Conclusion
Implementing two-factor authentication is no longer optional for WordPress websites concerned with security. The statistics clearly demonstrate the growing threat landscape, with plugins representing the primary vulnerability point. By adding this critical security layer, you significantly reduce the risk of unauthorized access and potential data breaches.
When selecting a 2FA plugin, prioritize solutions that balance strong security with good user experience. Consider your specific needs regarding authentication methods, user roles, and integration requirements. The plugins we’ve compared offer excellent starting points for most WordPress implementations.
Remember that 2FA is just one component of a comprehensive security strategy. Regular updates, security audits, and proper hosting configurations remain equally important. By implementing these measures together, you create a robust defense system that significantly reduces your vulnerability to common attack vectors.
As WordPress continues to evolve, security measures will adapt to meet new challenges. Staying informed about emerging threats and solutions ensures your website maintains strong protection against unauthorized access and potential compromise.
Next Steps for WordPress Security
- Evaluate your current WordPress security posture
- Select and implement an appropriate 2FA solution
- Create documentation and training for all users
- Establish recovery procedures for lost access
- Review and update your overall security strategy regularly
By taking these steps, you’ll significantly enhance your WordPress website’s security posture and protect your valuable digital assets from increasingly sophisticated threats.




